Table of Contents
There are many sources of information available in the form of mailing lists, RFCs and documentation. The documentation that comes with the Samba distribution contains good explanations of general SMB topics such as browsing.
With SMB networking, it is often not immediately clear what the cause is of a certain problem. Samba itself provides rather useful information, but in some cases you might have to fall back to using a sniffer. A sniffer is a program that listens on your LAN, analyzes the data sent on it and displays it on the screen.
One of the best diagnostic tools for debugging problems is Samba itself.
You can use the -d option for both smbd and nmbd to specify the
debug level at which to run.
See the man pages for smbd, nmbd and
smb.conf for more information regarding debugging options. The debug
level can range from 1 (the default) to 10 (100 for debugging passwords).
Another helpful method of debugging is to compile Samba using the
gcc -g flag. This will include debug information in the binaries and
allow you to attach gdb to the running smbd/nmbd process.
To attach gdb to an smbd
process for an NT workstation, first get the workstation to make the
connection. Pressing ctrl-alt-delete and going down to the domain box
is sufficient (at least, the first time you join the domain) to
generate a LsaEnumTrustedDomains. Thereafter, the workstation
maintains an open connection and there will be an smbd
process running (assuming that you haven't set a really short smbd
idle timeout). So, in between pressing ctrl-alt-delete and actually
typing in your password, you can attach gdb and continue.
Some useful Samba commands worth investigating are:
$testparm | more$smbclient -L //{netbios name of server}
Tcpdump was the first UNIX sniffer with SMB support. It is a command-line utility and now, its SMB support is somewhat lagging that of ethereal and tethereal.
Ethereal is a graphical sniffer, available for both UNIX (Gtk) and Windows. Ethereal's SMB support is quite good.
For details on the use of ethereal, read the well-written Ethereal User Guide.
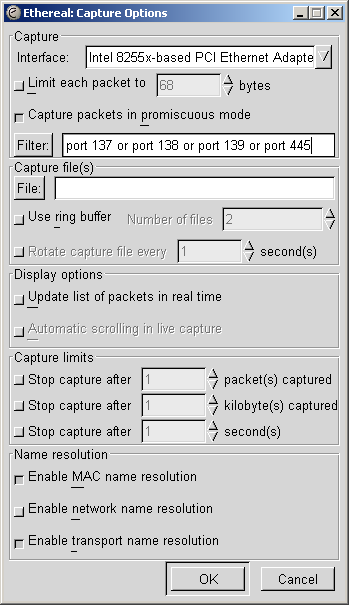
Listen for data on ports 137, 138, 139, and 445. For example, use
the filter port 137, port 138, port 139, or port
445 as seen in Starting a capture snapshot.
A console version of ethereal is available as well and is called tethereal.
For tracing things on Microsoft Windows NT, Network Monitor (aka Netmon) is available on Microsoft Developer Network CDs, the Windows NT Server install CD and the SMS CDs. The version of Netmon that ships with SMS allows for dumping packets between any two computers (i.e., placing the network interface in promiscuous mode). The version on the NT Server install CD will only allow monitoring of network traffic directed to the local NT box and broadcasts on the local subnet. Be aware that Ethereal can read and write Netmon formatted files.
Installing Netmon on an NT workstation requires a couple of steps. The following are instructions for installing Netmon V4.00.349, which comes with Microsoft Windows NT Server 4.0, on Microsoft Windows NT Workstation 4.0. The process should be similar for other versions of Windows NT version of Netmon. You will need both the Microsoft Windows NT Server 4.0 Install CD and the Workstation 4.0 Install CD.
Initially you will need to install Network Monitor Tools and Agent on the NT Server to do this:
Go to -> -> -> -> -> .
Select the Network Monitor Tools and Agent and click on .
Click on on the Network Control Panel.
Insert the Windows NT Server 4.0 install CD when prompted.
At this point, the Netmon files should exist in %SYSTEMROOT%\System32\netmon\*.*.
Two subdirectories exist as well, parsers\ which contains the necessary DLLs
for parsing the Netmon packet dump, and captures\.
To install the Netmon tools on an NT Workstation, you will first need to install the Network Monitor Agent from the Workstation install CD.
Go to -> -> -> -> -> .
Select the Network Monitor Agent, click on .
Click on in the Network Control Panel.
Insert the Windows NT Workstation 4.0 install CD when prompted.
Now copy the files from the NT Server in %SYSTEMROOT%\System32\netmon
to %SYSTEMROOT%\System32\netmon on the Workstation and set permissions
as you deem appropriate for your site. You will need administrative rights on the NT box to run Netmon.
To install Netmon on Windows 9x/Me, install the Network Monitor Agent
from the Windows 9x/Me CD (\admin\nettools\netmon).
There is a readme file located with the Netmon driver files on the CD if you need
information on how to do this. Copy the files from a working Netmon installation.
See how Scott Merrill simulates a BDC behavior at http://www.skippy.net/linux/smb-howto.html.
FTP site for older SMB specs: ftp://ftp.microsoft.com/developr/drg/CIFS/
There are a number of Samba-related mailing lists. Go to http://samba.org, click on your nearest mirror and then click on Support and next click on Samba-related mailing lists.
For questions relating to Samba TNG, go to http://www.samba-tng.org/. It has been requested that you do not post questions about Samba-TNG to the main-stream Samba lists.
If you do post a message to one of the lists, please observe the following guidelines :
Always remember that the developers are volunteers, they are not paid and they never guarantee to produce a particular feature at a particular time. Any timelines are “best guess” and nothing more.
Always mention what version of Samba you are using and what operating system it's running under. You should list the relevant sections of your
smb.conffile, at least the options in[global]that affect PDC support.In addition to the version, if you obtained Samba via CVS, mention the date when you last checked it out.
Try and make your questions clear and brief. Lots of long, convoluted questions get deleted before they are completely read! Do not post HTML encoded messages. Most people on mailing lists simply delete them.
If you run one of those nifty “I'm on holidays” things when you are away, make sure its configured to not answer mailing list traffic. Auto-responses to mailing lists really irritate the thousands of people who end up having to deal with such bad netiquet bahavior.
Don't cross post. Work out which is the best list to post to and see what happens. Do not post to both samba-ntdom and samba-technical. Many people active on the lists subscribe to more than one list and get annoyed to see the same message two or more times. Often someone will see a message and thinking it would be better dealt with on another list, will forward it on for you.
You might include partial log files written at a debug level set to as much as 20. Please do not send the entire log but just enough to give the context of the error messages.
If you have a complete Netmon trace (from the opening of the pipe to the error), you can send the *.CAP file as well.
Please think carefully before attaching a document to an email. Consider pasting the relevant parts into the body of the message. The Samba mailing lists go to a huge number of people. Do they all need a copy of your
smb.confin their attach directory?
To have your name removed from a Samba mailing list, go to the same place where you went to subscribe to it. Go to http://lists.samba.org, click on your nearest mirror, click on Support and then click on Samba related mailing lists.
Please do not post messages to the list asking to be removed. You will only be referred to the above address (unless that process failed in some way).