自行编写的基于iptable防御DDos攻击的插件
本软件能实现在受到DDOS的cc、syn半连接等功击时,进行比较有效的防御。实际上,它并不具备阻截能力,它是基于IPtables防火墙,利用netstat+过滤规则,与IPtables防火墙实现联动。在有恶意连接(例如syn flood)攻击服务器指定端口时,本软件会实时分析连接来源的企图。当连接IP有多并发恶意连接时,软件自动将其加入iptables防火墙条目进行阻截。同时将攻击IP记录到计划解封文件里,当达到预定时间后,软件自动从IPtables防火墙中解封对应IP。
本软件利用了一周时间写完,在基本测试过程中,表现还可以。但不排除有BUG的可能。应付单IP并发连接攻击、单IP的syn flood等效果明显。由此可见,它也不适合于随机IP的恶意攻击。
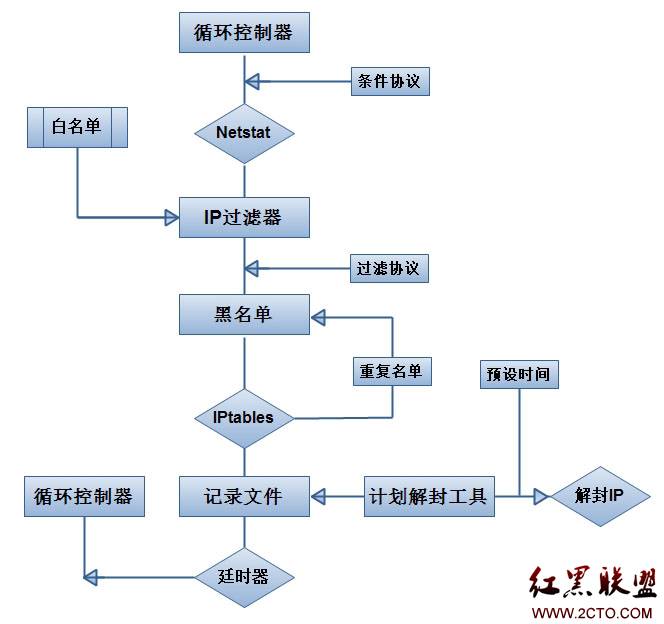
系统结构图
安装使用:
本软件安装方式十分简单,下载软件后解压(tar zxvf DDos_firewall-v1.0.0.tar.gz),进入主目录,找到autosetup.sh,运行自动安装即可!
运行环境:
centos 32bit or 64bit 、redhat 32bit or 64bit、fedora 32bit or 64bit,其他linux未测试。
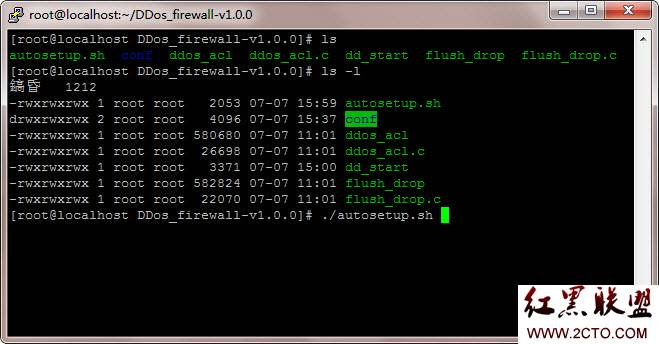
启动方式:
dd_start {start|stop|restart|status}
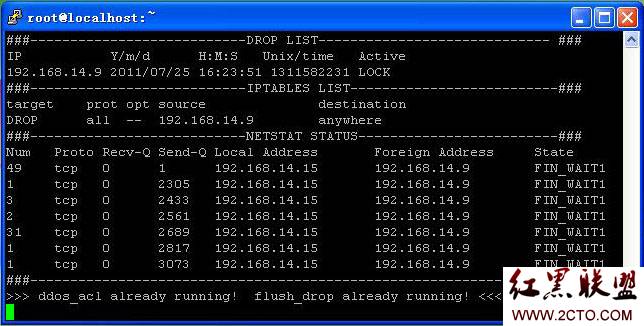
运行状态/IP封锁图
配置实例:
#############################################
### FileName:ddos_drop.conf
### Auth:Sunshine Gu
### http://blog.hit008.com
### ddos_acl and flush_drop config file.
#############################################
[main setting]
### Main directory
filepath=/usr/local/ddos_drop
### Pid file
ddos_acl_pidfile=/usr/local/ddos_drop/logs/ddos_acl.pid
flush_drop_pidfile=/usr/local/ddos_drop/logs/flush_drop.pid
### Temporary blacklist
grep_list=/usr/local/ddos_drop/logs/drop_ip.dat
### Plans to remove(blacklist)
crond_list=/usr/local/ddos_drop/logs/crond_list.dat
### Temporary file,used to clean blacklist queue in crond_list.
temp_list=/usr/local/ddos_drop/logs/temp_list~
### White list
else_list=192.168.14.15|127.0.0.1|0.0.0.0
### Monitor port
grep_port=80|8080|443
### Executive frequency(s)
exec_time=10
### Lock time,used to lock blacklist in grep_list,
### Over this time, iptables will automatically delete.(s)
acl_cls=3600
《Shell源码开源》
1. 主守护程序,ddos_acl.sh
#!/bin/sh
########################################
### FileName: ddos_acl.sh
### Auth: Sunshine GU
### Version: v1.0.0
### http://blog.hit008.com
########################################
############################################载入配置文件########################################
###文件主目录[filepath]
###PID文件[pidfile]
###临时黑名单[grep_list]
###计划清除队列[crond_list]
###白名单[else_list]
###监控端口[grep_port]
###执行频率(s) [exec_time]
conffile=../conf/ddos_drop.conf
if [ -e $conffile ];then
#cat $conffile|awk -v key="main" -v RS='\\[[^\n]*]' 'v=="["key"]";{v=RT}'|sed 's/ //g'|sed -r '/^ *#.*/d;s/ *#.*//'
filepath=`grep 'filepath=' $conffile|sed 's/ //g'|sed -r '/^ *#.*/d;s/ *#.*//'|awk -F = '{print $2}'`
ddos_acl_pidfile=`grep 'ddos_acl_pidfile=' $conffile|sed 's/ //g'|sed -r '/^ *#.*/d;s/ *#.*//'|awk -F = '{print $2}'`
flush_drop_pidfile=`grep 'flush_drop_pidfile=' $conffile|sed 's/ //g'|sed -r '/^ *#.*/d;s/ *#.*//'|awk -F = '{print $2}'`
grep_list=`grep 'grep_list=' $conffile|sed 's/ //g'|sed -r '/^ *#.*/d;s/ *#.*//'|awk -F = '{print $2}'`
crond_list=`grep 'crond_list=' $conffile|sed 's/ //g'|sed -r '/^ *#.*/d;s/ *#.*//'|awk -F = '{print $2}'`
temp_list=`grep 'temp_list=' $conffile|sed 's/ //g'|sed -r '/^ *#.*/d;s/ *#.*//'|awk -F = '{print $2}'`
else_list=`grep 'else_list=' $conffile|sed 's/ //g'|sed -r '/^ *#.*/d;s/ *#.*//'|awk -F = '{print $2}'`
grep_port=`grep 'grep_port=' $conffile|sed 's/ //g'|sed -r '/^ *#.*/d;s/ *#.*//'|awk -F = '{print $2}'`
exec_time=`grep 'exec_time=' $conffile|sed 's/ //g'|sed -r '/^ *#.*/d;s/ *#.*//'|awk -F = '{print $2}'`
acl_cls=`grep 'acl_cls=' $conffile|sed 's/ //g'|sed -r '/^ *#.*/d;s/ *#.*//'|awk -F = '{print $2}'`
else
echo "Can't find the configuration file!"
exit 1
fi
################################################################################################
###清空旧的非法IP
if [ -d $filepath/logs ];then
if [ -f $grep_list ];then
rm -f $grep_list
fi
else
mkdir $filepath/logs
fi
###根据连接状态进行IP屏蔽
echo "$$" > $ddos_acl_pidfile
while true
do
#根据连接数反应恶意连接,并记录连接ip
/bin/netstat -ant |grep -E $grep_port|awk '{print $5}'|awk -F : '{print $1}'|sort|uniq -c|sort -rn|grep -v -E $else_list|awk '{if ($2!=null && $1>100) {print $2}}' > $grep_list
if [ -f $grep_list ];then
#遍历不重复的条目
for i in `cat $grep_list|uniq -c|awk '{print $2}'`
do
#要求iptables没有重复条目
if [ `iptables --list|grep $i|wc -l` -eq 0 ];then
#记录非法IP信息,并进行封闭
echo "$i `date +%Y/%m/%d` `date +%H:%M:%S` `date +%s` LOCK" >> $crond_list
/sbin/iptables -I INPUT -s $i -j DROP;
else
continue
fi
done
fi
sleep $exec_time
done
2. 计划解封程序,flush_drop.sh
#!/bin/sh
########################################
### FileName: flush_drop.sh
### Auth: Sunshine GU
### Version: v1.0.0
### http://blog.hit008.com
########################################
############################################载入配置文件########################################
###文件主目录[filepath]
###PID文件[pidfile]
###临时黑名单[grep_list]
###计划清除队列[crond_list]
###白名单[else_list]
###监控端口[grep_port]
###执行频率(s) [exec_time]
conffile=../conf/ddos_drop.conf
if [ -e $conffile ];then
#cat $conffile|awk -v key="main" -v RS='\\[[^\n]*]' 'v=="["key"]";{v=RT}'|sed 's/ //g'|sed -r '/^ *#.*/d;s/ *#.*//'
filepath=`grep 'filepath=' $conffile|sed 's/ //g'|sed -r '/^ *#.*/d;s/ *#.*//'|awk -F = '{print $2}'`
ddos_acl_pidfile=`grep 'ddos_acl_pidfile=' $conffile|sed 's/ //g'|sed -r '/^ *#.*/d;s/ *#.*//'|awk -F = '{print $2}'`
flush_drop_pidfile=`grep 'flush_drop_pidfile=' $conffile|sed 's/ //g'|sed -r '/^ *#.*/d;s/ *#.*//'|awk -F = '{print $2}'`
grep_list=`grep 'grep_list=' $conffile|sed 's/ //g'|sed -r '/^ *#.*/d;s/ *#.*//'|awk -F = '{print $2}'`
crond_list=`grep 'crond_list=' $conffile|sed 's/ //g'|sed -r '/^ *#.*/d;s/ *#.*//'|awk -F = '{print $2}'`
temp_list=`grep 'temp_list=' $conffile|sed 's/ //g'|sed -r '/^ *#.*/d;s/ *#.*//'|awk -F = '{print $2}'`
else_list=`grep 'else_list=' $conffile|sed 's/ //g'|sed -r '/^ *#.*/d;s/ *#.*//'|awk -F = '{print $2}'`
grep_port=`grep 'grep_port=' $conffile|sed 's/ //g'|sed -r '/^ *#.*/d;s/ *#.*//'|awk -F = '{print $2}'`
exec_time=`grep 'exec_time=' $conffile|sed 's/ //g'|sed -r '/^ *#.*/d;s/ *#.*//'|awk -F = '{print $2}'`
acl_cls=`grep 'acl_cls=' $conffile|sed 's/ //g'|sed -r '/^ *#.*/d;s/ *#.*//'|awk -F = '{print $2}'`
else
echo "Can't find the configuration file!"
exit 1
fi
################################################################################################
echo "$$" > $flush_drop_pidfile
while true
do
sleep $exec_time
#取得当前时间
nowtime=`date +%s`
#文件是否存在
if [ -e $crond_list ];then
#遍历所有条目
for i in `awk '{print $1}' $crond_list`
do
#内容不为空
if [ `cat $crond_list|wc -l` -ne 0 ];then
#单次最多取出一条,排除重复条目
ti=`grep $i $crond_list|awk '{print $4}'|head -1`
b=`expr $nowtime - $ti`
#判断是否超规定时间
if [ $b -gt $acl_cls ];then
#iptables里存在条目
if [ `iptables --list|grep $i|wc -l` -ne 0 ];then
/sbin/iptables -D INPUT -s $i -j DROP
fi
#清除crond_list的当前条目
cp $crond_list $temp_list
sed -e "/$i/d" $temp_list > $crond_list
rm -f $temp_list
fi
fi
done
fi
done
3. 主启动程序,dd_start.sh
#!/bin/sh
#############################################
### FileName:autosetup.sh
### Auth:Sunshine Gu
### Version: v1.0.0
### http://blog.hit008.com
### Bash shell for start DDos_Drop.
#############################################
### Main directory
filepath=/usr/local/ddos_drop
### Program name
DAEMON=$filepath/bin/ddos_acl
FLUSHIP=$filepath/bin/flush_drop
### Plans to remove(blacklist)
crond_list=$filepath/logs/crond_list.dat
### White list
else_list='127.0.0.1|0.0.0.0'
### Monitor port
grep_port='80|8080|443'
### Pid file
pidfile1=$filepath/logs/ddos_acl.pid
pidfile2=$filepath/logs/flush_drop.pid
set -e
[ -x "$DAEMON" ] || exit 0
do_start() {
if [ `pgrep -f 'ddos_acl'|wc -l` -eq 0 ];then
$DAEMON &
$FLUSHIP &
else
echo -e "ddos_acl already running!"
exit 1
fi
}
do_stop() {
if [ `pgrep -f 'ddos_acl'|wc -l` -eq 0 ];then
echo -e "ddos_acl not running!"
else
kill -9 `cat $pidfile1`
fi
if [ `pgrep -f 'flush_drop'|wc -l` -eq 0 ];then
echo -e "flush_drop not running!"
else
kill -9 `cat $pidfile2`
fi
if [ `pgrep -f 'flush_drop'|wc -l` -ne 0 ]&&[ `pgrep -f 'flush_acl'|wc -l` -ne 0 ];then
kill -9 `cat $pidfile1`
kill -9 `cat $pidfile2`
rm -rf $pidfile1 $pidfile2
fi
}
do_restart() {
do_stop
do_start
}
do_status() {
echo "###---------------------------DROP LIST----------------------------- ###"
echo "IP Y/m/d H:M:S Unix/time Active"
if [ -e $crond_list ];then
cat $crond_list
else
echo "no information..."
fi
echo "###---------------------------IPTABLES LIST--------------------------###"
echo "target prot opt source destination"
iptables --list|grep 'DROP'|awk {'printf "%-10s%-5s%-4s%-20s%-11s\n",$1,$2,$3,$4,$5'}
echo "###---------------------------NETSTAT STATUS-------------------------###"
echo "Num Proto Recv-Q Send-Q Local Address Foreign Address State"
netstat -ant |grep -E $grep_port|grep -v -E $else_list|sed 's/:/ /g'|awk '{print $1,$2,$3,$4,$6,$8}'|sort|uniq -c|awk '{printf "%-6s%-06s%-07s%-07s%-20s%-20s%-10s\n",$1,$2,$3,$4,$5,$6,$7}'
echo "###------------------------------------------------------------------###"
if [ `pgrep -f 'ddos_acl'|wc -l` -ne 0 ];then
echo -n ">>> ddos_acl already running! "
else
echo -n ">>> ddos_acl not running! "
fi
if [ `pgrep -f 'flush_drop'|wc -l` -ne 0 ];then
echo " flush_drop already running! <<<"
else
echo " flush_drop not running! <<<"
fi
}
case "$1" in
start)
echo -e "Starting ddos_acl ..."
do_start
echo "Done."
;;
stop)
echo -e "Stopping ddos_acl ..."
do_stop
echo "Done."
;;
restart)
echo -e "Restarting ddos_acl ..."
do_restart
echo "Done."
;;
status)
while true
do
clear
do_status
sleep 3
done
;;
*)
echo $"Usage: $prog {start|stop|restart|status}"
exit 1
esac
软件需安装到指定路径下(/usr/local/),安装好的目录有:
/usr/local/ddos_drop/bin,为执行文件目录
/usr/local/ddos_drop/conf,配置文件目录
/usr/local/ddos_drop/logs,记录文件目录
提供下载的为打包C文件,需要经过gcc编译。启动autosetup.sh 即可完成gcc编译和安装!
软件:DDos Firewall-v1.0.0
-
 在CentOS6.x下安装Compiz——桌面立方体,特效种种
在CentOS6.x下安装Compiz——桌面立方体,特效种种
-
 利用U盘安装windows7
利用U盘安装windows7
-
 sqlserver查询数据可编辑方法
sqlserver查询数据可编辑方法
-
 Android RoboGuice使用指南(7):@Provides Methods
Android RoboGuice使用指南(7):@Provides Methods
- 文章
- 推荐
- 热门新闻